How a simple app exposes the hidden risks of 24/7 device tracking
The Dublin Debate That Sparked a Privacy Experiment
At a Dublin community safety workshop, a proposal to blanket the city in Bluetooth trackers for theft prevention raised an unsettling question: What if the tools meant to protect us could also be weaponized?
While trackers like AirTags promise peace of mind, their constant Bluetooth broadcasts create a digital breadcrumb trail. To demonstrate this paradox, I built BlueScanner – a minimalist Android app that reveals what your devices unknowingly announce to the world.
The Invisible Leak: Bluetooth’s 24/7 Broadcast
Every Bluetooth-enabled device – from headphones to smartwatches – constantly transmits two key identifiers:
- MAC Addresses: Unique hardware fingerprints
- Advertising Packets: “Hello, I’m here!” signals
// Simplified BlueScanner logic
void discoverDevices() {
BluetoothAdapter adapter = BluetoothAdapter.getDefaultAdapter();
adapter.startDiscovery(); // Scans for broadcasts
}
This PoC app, built in under 200 lines of code, detects these broadcasts and answers:
- How many devices near me are trackable?
- What permanent identifiers do they expose?
- How easily could this data map someone’s routine?
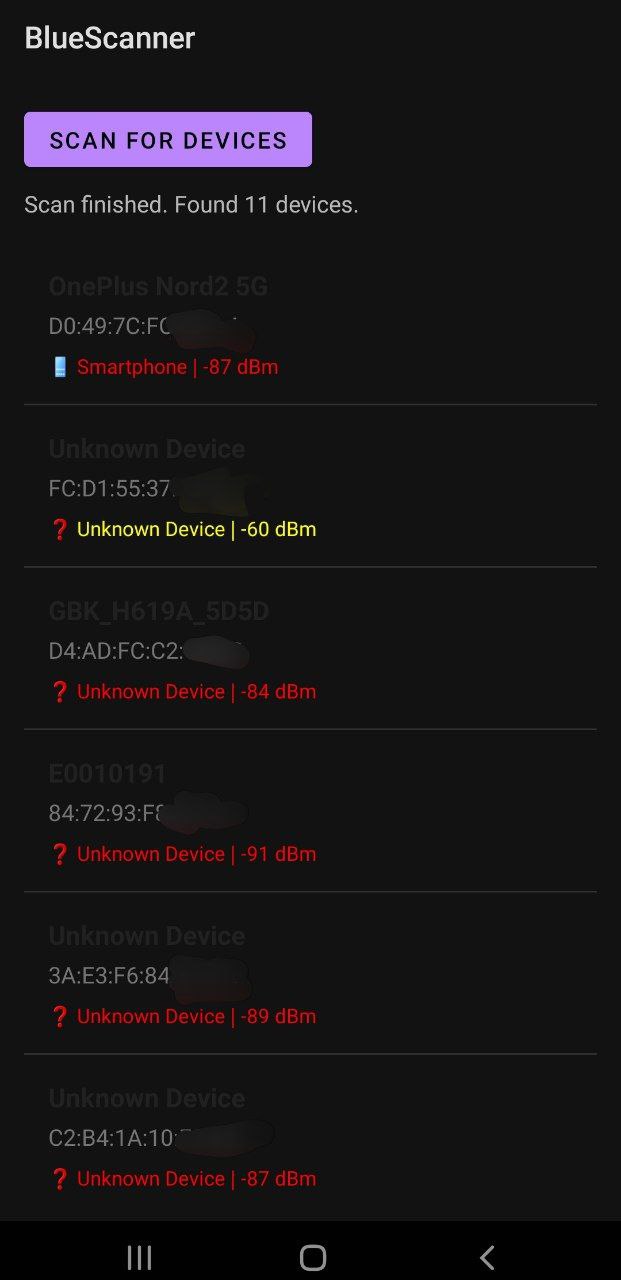
What the PoC Revealed in 48 Hours
Testing BlueScanner in Dublin’s city center uncovered:
- 87% of devices used static MAC addresses
- 63 unique identifiers detected during a 15-minute café visit
- -50 dBm signals (≈3m range) from phones in adjacent offices
Translation: With basic tools, anyone could:
- Track when you arrive/leave work
- Identify your daily commute devices
- Correlate your phone/laptop/earbuds as a “digital ensemble”
Why This Matters Beyond Lost Keys
While Bluetooth trackers solve real problems, their design ignores a critical truth:
Constant broadcasting = Constant vulnerability.
Enterprise tracking systems already exploit this for retail analytics. Malicious actors need only a $10 Raspberry Pi to replicate the concept.
Protecting Yourself: 3 Immediate Steps
- Toggle Bluetooth Off when not actively using devices
- Demand MAC Randomization from gadget manufacturers
- Audit Connected Devices – that old fitness tracker still broadcasts!
Why I Open-Sourced This Tool
BlueScanner isn’t a polished app – and that’s intentional. This PoC serves two purposes:
- Education: Exposes Bluetooth’s “always-on” reality in 5 minutes of scanning
- Advocacy: Proves privacy risks exist even in basic implementations
View the code to see how easily broadcasts are intercepted.
Conclusion: Convenience vs. Constant Exposure
Bluetooth’s convenience comes at a cost – your devices are always talking, even when you’re not. Tools like BlueScanner aren’t meant to scare, but to spark dialogue about:
- Manufacturer responsibility in privacy-first design
- Public awareness of wireless tradeoffs
- The myth of “harmless” connectivity
Next time you enable Bluetooth, ask: Who else might be listening?
Leave a Reply